Introduction
Email security is something we get a significant amount of questions about. Be it for various scams, ransomwares, hacked email credentials and more.
We currently live in the era of data breaches and figured it's probably important to talk about these and how they may affect your email security.
Your password might be out there
Let's talk about data breaches.
Dumping databases is a very common hacking goal and some people exclusively aim to do just that. The amount of known or unknown database dumps sitting around in obscure or not-obscure-enough places is staggering.
Not to give you a complete history of the biggest breaches in history, but here are a few well known ones for services that we know many of our customers probably use:
- Linkedin — More than 100 million accounts were compromised somehwere around 2012 (though the leak became public knowledge much later on). Email addresses and their corresponding hashed password were leaked.
- Dropbox — Dropbox forced a password reset for all of their account following a massive breach of email addresses and hashed passwords.
- Adobe accounts — An example of a software company suddenly asking you to create an account to use their software, for it to end up in a data breach later on. We're talking 153 million email addresses and hashed passwords (password hints were also leaked).
- Tumblr and Myspace — These probably aren't of much interest to most of our customers but the idea is to show that even social media sites are affected. Even though the Myspace breach is old (around 2008) it's 360 million email addresses and hashed (since then decrypted) passwords.
What's a hashed password?
You may have noticed we talked about hashed passwords a lot in the small data breach list above. A password hash is a representation of the actual password after going through a hashing function.
Hash functions are one-way mathematical bitwise manipulations which output a fixed-length representation of the original password but it's not longer possible to derive the original password from that representation.
We could compare its principles to applying the pixelize filter to an image. Applying the same filter to the same image yields the same pixelized result, but we can't derive the original image from the pixelized result, it's a one way process creating a "signature" or "digest" of the original value.
Companies that store access credentials almost always store hashed versions of passwords and compute the hash of the password you type to login to compare it against the hash they have in their database.
When a password is being moved around in a network or stored in an operating system (like your Windows password) they're also password hashes. Any hacker successfully dumping a database from a local computer or website would only have the hashed passwords and not the original, actual passwords and thus cannot use the hashes to impersonate anybody from the data dump.
Ideally, finding out what the corresponding password is by just having the hash is impossible. In practice that's not exactly true.
There are several different hashing functions, some of which produce weaker results in terms of mathematical dispersion. As hashes are often fixed in length but created from a source of arbitrary length, it's technically possible to have more than one source producing the same hash.
There are also specific attacks that pertain to hashing functions, which are mitigated by adding a salt to your password before calculating the hash (you don't have any control over this as an end user). That salt is an arbitrary value that is stored somewhere alongside your password hash in the company database. Some companies also use multiple iterations of hashing but these do not concern the end user, altough you have to keep in mind that when registering to a service online, you have no idea how far they have pushed their password obfuscation and that they could even be keeping everything in clear text.
Even with no specific attack vector you could just compute the hash of every possible character combination and compare it against leaked hashes until you find the corresponding password.
That might sound like an impossible endeavor since an 8-character long password with special characters, upper and lowercase letters and numbers yields 457 163 239 653 376 different possibilities but some estimates come to as low as about 2.6 days to crack with a special password cracking system that can be put together online using cloud computing services.
With dedicated on-premise password cracking rigs using many graphic processing units this can be even faster. Check out howsecureismypassword.net and try typing out a strong, 8 letters password and see how much cracking time gets estimated. I've seen as low as 2 seconds, and that's due to these rigs being able to compute a great many hashes in parallel.
The data breaches also have another side effect: they generate high confidence statistical data about the most used passwords. These common passwords can be tested first (before attempting to compute every possible hash) and may yield immediate results. This is why typing "password" on howsecureismypassword.net will yield "Instantly".
The point is, some password hashes might be harder to crack than others but they're all vulnerable, especially when many of these breaches have been around for years.
The cracking of a hash is sometimes called decrypting the hash even though hashing is technically not encryption.
So what exactly is out there?
For all the leaks we listed above, the password hashes have been cracked which means a lot of email addresses with their corresponding password at the time are compromised.
Recent data breaches are usually sold on black markets and thus aren't public for what it's worth. But breaches such as the LinkedIn one have their data readily available, on the so called darknet but also on the general public Internet with all the passwords in cleartext.
The reality is actually much worse than that, as there are databases floating around containing more than one billion of matching email addresses and cleartext passwords and these are not super hard to find as they are common research material for artifical intelligence research projects. The more responsible projects will only use the password list (without the associated emails) but everything is always available somewhere (for free, I might add).
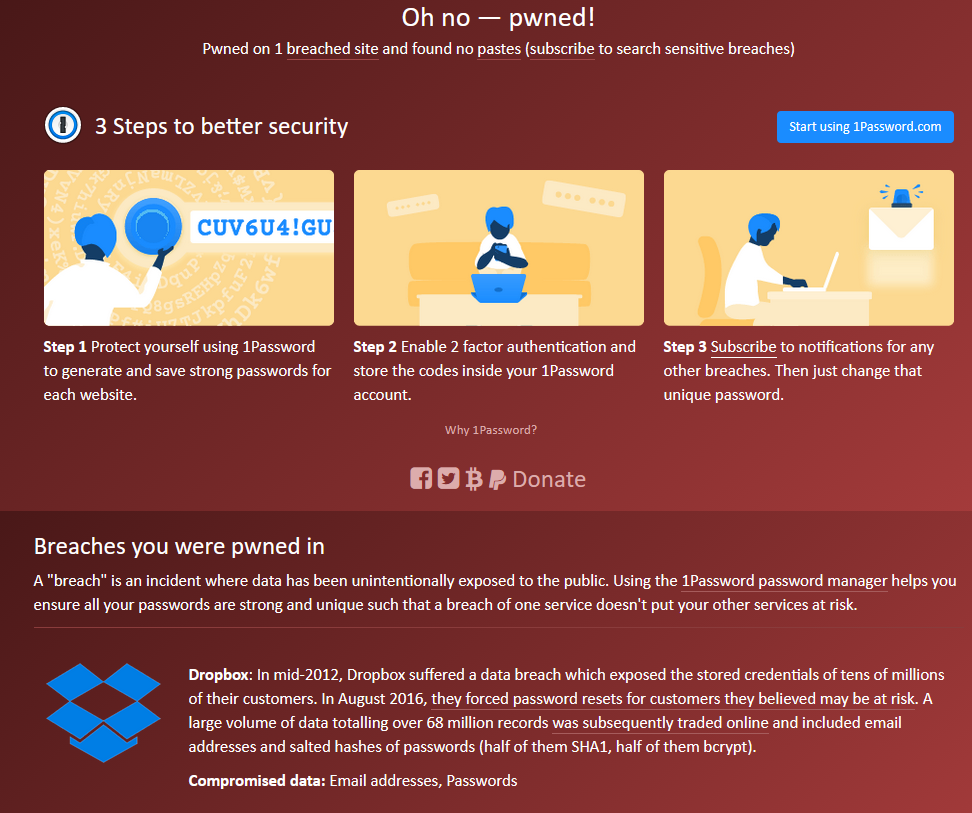
There is a great and easy to share around tool made by security expert Troy Hunt which allows you to check if a given email address has been seen in a known data breach at this time.
The site is called haveibeenpwned.com.
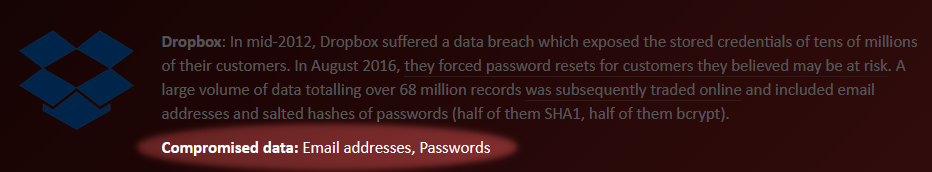
Just type in your email addresses and check if you're in the green or not. When an email address was found in a data breach, haveibeenpwned.com will also tell you which one, as shown in the example below:
In this case, the address was found in the Dropbox breach. The site also lists what data was compromised, which is extremely useful. Basically, if you see passwords (whether hashed or not) in there, your password is out there. Believe me. It is.
Maybe you don't use that password with that specific email address anymore but you probably still use that password somewhere. A dedicated hacker could dig through all of your online life and try that password on every single account you might have.
There's a reason why big actors like Microsoft, Google and Facebook now detect people trying to log into an account from an unusual place or unknown device, these extra steps are meant to protect you against connection attempts with leaked passwords.
However, you should not have unlimited trust in these mechanisms as sometimes there are still ways to game the system by manually impersonating you and contacting their support or answering the "secret questions" among other personnal information that may be readily available.
Here's an example warning email after a suspicious login to a Yahoo account:
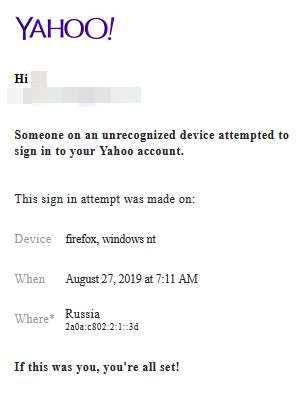
These aren't always clear, as the login attempt here was indeed unsuccessful, but the actual correct password was used for it, which is the more alarming part that should be mentioned.
From what I've tested on Outlook.com and Gmail.com, it looks like they have implemented the same protections when you try to login via the IMAP or POP protocol, which is great. Other providers might have forgotten about that login channel and left that door wide open.
Some big actors like Twitter (some gaming services like uPlay also come to mind) have very poor unusual login protections. Do not automatically trust any website to have these in place.
What do I do if my email account is compromised?
You should change your password.
Try to list any account for which you may have used that same password, as they all need to be changed. This includes your home wifi password.
You have probably already seen advice not to reuse passwords, it would effectively reduce the risks in case of a data breach, and you should always assume a data breach is possible.
We touch on more possibilities to harden your personnal security in the best practices section below.
In the case of Net7 email account, there is an indirect protection in that the email address used for logging into the email services is usually different from the main alias you use as your public email address.
This means that someone with your password and your main email alias still can't connect to your mailbox because they don't have your exact account name.
As a result, you should not use the main account name as your "from" email address and always use an alias.
Moreover, you could create more aliases and use different ones for different accounts.
If possible, you should use long passphrases instead of a password. Something longer than 12 characters is exponentially harder to crack than an 8-character password, even for a high end cracking rig. It doesn't have to be arbitrary characters, the cracking rig doesn't care if it is or not, you can just use a phrase (hence the term passphrase) - Just make sure it's hard to guess in the case the attacker knows you personally.
Example passphrase: ihadhairwheniwasborniswear
See how such a password is rated on howsecureismypassword.net:
Finally, you can register your email on haveibeenpwned.com to have them notify you in case your email ends up in a breach in the future.
About email scams and data breaches
Email scamming was around way before the golden age of the data breach. We've all seen the classic Nigerian princes inheritance notices and other so called "lotteries" somehow organized by Bill Gates.
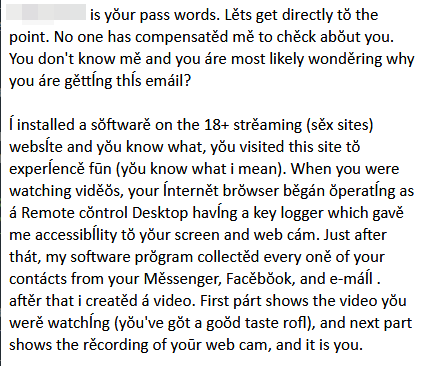
Although it's also nothing new for scammers to try and appeal to shame by claiming they have nudes of you or weirdly specific videos taken by your highjacked webcam, the data breaches made it a little more realistic lately as we can now sometime get scams mentioning what is effectively one of your passwords. It may even be the exact password for the email account on which you received the scam.
Here's an example where my password was the first word:
These passwords in clear text come from data breaches (yes, those with hashed passwords) and they can make these scams more believable to some people.
Other common attack vectors
Data breaches are not the only thing that can lead to an account being compromised. Here are a few other possible attack vectors.
Public Wifi
Although any network can technically be tempered with to allow someone to intercept your traffic, this is especially true of any wifi network and it doesn't require any tempering, just some tech knowledge and packet sniffing software.
Anyone currently connected to the same wifi as you can see all the network packets your computer or phone is sending or receiving.
When browsing the web using HTTPS (websites with the green (grey on recent Chrome versions) padlock icon) your traffic is encrypted, so they can't see the content being transferred although there is still info they could derive by analysing your traffic (e.g. which website you're contacting, what kind of volume, etc.).
You should always be extra careful on any public wifi:
- Use encrypted protocols: HTTPS for the web, and email protocols that are secure - Use the webmail if you're not sure you have these setup on your email client and DO NOT START YOUR EMAIL CLIENT as it might attempt to fetch emails unsecurely immediately
- Never use basic FTP connections from there - It transfers passwords in clear text
When browsing the web, be it your webmail or anything else, double check that the HTTPS padlock is always there because there is such a thing as SSL stripping although the risk is very low.
Please shoot us an email if you'd like to know how to setup secure email protocols to use with your email clients such as Outlook or Thunderbird — please specify which inbound email server you're using in your request.
Malware and viruses
Your computer stores password hashes locally but much worse than that, you might also have cleartext passwords on your hard drive with no safeguards to accessing it using a normal user account.
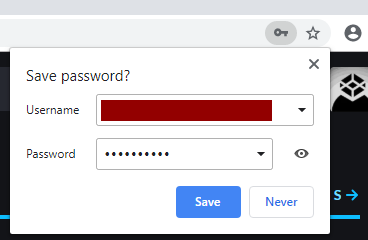
The main culprits are web browsers. When you enter a password online, they ask if you want that password to be saved for next time. Doing this actually puts the plain text password somewhere on your local system, which a malware could harvest and send to malicious actors. They don't even need to crack the hash, they already have your password.
Most malware is very plain and simple software. In Windows terms, they are .exe files that you ran on your system directly or indirectly.
The solution here is to only start programs you trust and if at all possible do not save passwords in clear text on your computer which means not saving passwords in web browsers or any other apps such as an email of FTP client.
The Windows account passwords are also vulnerable (in hashed form). Linux and Mac systems are usually safer in that domain because their local password database are not visible by non-administrator users and they don't keep hashes of password in memory (at least they shouldn't - It might happen). Then again, most malware does not target Linux or Mac anyway.
It's common for malware to disguise as legitimate software, sometimes even claming to be malware-removal software.
You don't have to go overboard with antivirus software as they have been shown to sometimes even compromise your security — the antivirus included in Windows 10 is potent enough as they have made significant security investments since the days of Windows XP.
More complex malware, such as many instances from the family ransomware, usually take advantage of a vulnerability in Windows (or more rarely in mobile phone software). The main protection against these is to always keep your operating system up to date.
The extremely frequent Windows updates nagging you to reboot your computer or just doing it for you are very often about protecting you from these vulnerabilities.
A good news when it comes to password security is that nowadays most malwares are ransomware which encrypt the content of your hard drive and don't actually steal any data. Malware scammers tend to gravitate to what is the most lucrative at the moment.
Phishing
Phishing is about mimicking an email from a legitimate source, most of the time banks or social networks (Paypal also comes to mind), asking you to "Review your account policy" or "Unlock your account" or something along these lines.
They can spoof a legitimate email address or use a domain they own that is very close to the real thing.
In effect the link in the fake email takes you to a copy of the real website and asks you for your credentials.
Phishing can be much more targetted and dirtier than that, we have seen phishing attempts to company email trying to pass as that company itself (claming to be internal IT support is a classic). They can also attach a .docx or .pdf file with a security exploit in it in the hope of having it take control of the person's computer and tactics to have you open the attachment are varied and may target the specific department that person is working for.
Because of phishing, most official emails from a company will not contain links to login pages of whatnot. When you click on such a link, be extra mindful of the presence of a valid HTTPS connection.
HTTPS serves two main purposes:
- Authentication — Making sure the server at that domain name has really been verified to be the server for that domain name
- Encryption — Encrypt all communication from client to server and protect against man-in-the-middle attacks
A website with a broken HTTPS padlock means the authentication part failed, the encryption might be perfectly fine if not done using weak ciphers.
Without going into details for the authentication mechanism, you should probably know that it's possible to temper with your local web browser to have it show unlawful destination servers as authenticated. You should not allow anything or anyone to temper with your web browser and operating system certificate stores unless it's absolutely required by company policy.
Last but not least, just don't open fishy attachments. This is especially true if you're trying to hide your location or identity, as even a video file could betray your real IP address by contacting some cryptic fake DRM server.
Social engineering
Picture someone having found your password in a data breach but it's attached to an email address that has two-factor authentication enabled (it sends you a SMS with a one-time code when you try to log in).
They can't hack into your email because they don't have access to your phone. But what if they called you pretending to be from your company IT department and tell you something like:
I'm X from the IT department, I'm running a migration of software Y and would need a code that you should receive on your phone in a moment. I would never ask your password, though, and you should never give your password to anyone.
You might be enclined to trust that person and give them the one-time code. Some phone scams have convinced people they were their bank and have them go through the whole connection process to their online banking, complete with 2-factor authentication as well.
Social engineering is very targetted hacking but you should be mindful of it as data breaches can add a new twist to it by having the attacker already know your password or other personnal information (such as secret questions).
Sometimes it's not you getting the social engineering but your IT support or us (Net7). For instance, we have seen stories where people have succeeded in removing the two-factor authentication from a service by calling support and trying to convincingly pass as the actual customer.
Social engineering is the main reason why some hardened security measures, like two-factor authentication or even biometrics, can sometimes fail at their mission. Nothing is ever 100% secure.
Brute forcing
We have seen that data breaches effectively produced databases of more than one billion passwords. From there, it's easy to infer the most commonly used ones, vary around these, maybe add the current year or some two digit number.
Password lists can be used against you to attempt to login on a webmail, IMAP or POP email services.
The existence of brute forcing with password lists is the reason why you're asked to use a "complex" password with special characters, uppercase letters etc. for most online services.
One of the oldest password list came from a data breach on the now defunct RockYou service and is often cited in security material and training as the "rockyou" password list (the Kali Linux distribution comes preinstalled with it). You can easily find it on Google if you want to have a look at what passwords not to use. It's so widespread that some services will check if your chosen password is in the "rockyou" list before accepting it or not.
123456
12345
123456789
password
iloveyou
princess
1234567
rockyou
12345678
abc123
nicole
daniel
babygirl
monkey
lovely
jessica
654321
michael
ashley
qwerty
111111
iloveu
000000
These are some of the most common passwords as seen in the "rockyou" list. We can see "password" is actually the 4th most used password for real.
Password list brute force attacks could be made more complex than just going through the "rockyou" list using the most common passwords first, some of them might try all kind of combinations as well so keep in mind that adding a number after your very common password won't make it secure.
Best practices
Use passphrases or long passwords
We talk about it at length in a previous section.
When the service allows it, having a password of at least 12 characters has more impact than trying to mix up special characters and uppercase letters and whatnot on a smaller password.
Don't save credentials locally
For POP and IMAP, which are email protocols that periodically check for new email, it's not really practical to enter your password every X minutes.
At least remember to do it only on trusted computers. Anywhere else, please use the webmail over HTTPS.
Keep in mind that having your browser "remember passwords" means it's saving them in plain text somewhere.
Use a password manager
Password managers help you keep track of all your passwords in an encrypted file.
You just need to remember your master password.
This makes it easier to vary your passwords for every account and even generate pseudo-random ones.
LastPass is probably the most well known. Its parent company, Logmein, employs a large amount of high profile security experts. Doesn't mean you should just trust me on this or that we endorse LastPass, you check it out for yourself and read more about it if interested.
Authenticate using one of the big actors
Some services will allow you to Login with Facebook, Login with Google or other similar big fishes. Provided they only ask for your account password on the actual authenticated corresponding account domain (which means the password prompt for your Facebook account is in a window showing up https://www.facebook.com/* in the address bar), this is arguably safer than creating a new account there.
It means your password is not stored in any shape or form on the database for that service. It stays at Facebook, Google, or whatever else you're using. Which means that in case of a data breach, they don't have your password (they might have your email and possibly other personnal information though).
Big companies like Facebook have had leaks in the past, but since these global authentication actors have very heavily invested in security and depend on that for their very reputation, there is a low chance of something such as a Google account data breach happening.
Here is an example on the Glitch.com website that offers signing in with Facebook, Github and Google. The "Sign in with email" option is the only one where they will have your password in their database.
Of course and especially in the case of Facebook, the app might ask for permissions to get information from your profile. I personally prefer avoiding using Facebook for signing in for that reason.
Some companies go even further than Glitch.com and don't even propose a in-house email based sign in option. Now you know they don't do it by laziness but more probably because they really want to avoid having passwords in their databases to limit the damage in case of a data breach.
Use two-factor authentication
Most if not all of the large online companies offer at least one way to do multifactor authentication which is probably the security measure with the highest risk reduction to cost of implementation ratio.
Most online banking services also use multifactor authentication. It sometimes requires a device, a specific application installed on a mobile phone, or it may involve receiving a SMS message or even an email, in its simplest form (which is still pretty effective against unlawful login attempts).
For instance, in your Microsoft account security page, you should be able to find the option (it's not always in plain sight):
The main weakness of these systems are social engineering. It's common to switch mobile phones or change phone number and thus breaking the possibility to use two-factor authentication, which requires you to contact the tech support for that company and try to have them remove the previous authenticator.
Sometimes you can pick multiple two-factor avenues and sort it out without human intervention, which is always more secure.
Use encrypted protocols
We touched on that multiple times during this article. Try to always use encrypted protocols for everything.
About the email specifically, when not sure, use the webmail in HTTPS to send and receive.
This is especially important when you're on a public or unknown network.
Update your software
Make sure the Windows updates get applied. Install updates for your Office software, PDF reader, etc.
Keep your email client and web browser up to date as well (already automatic by default for the latter).
Don't forget your phone: make sure to apply system updates when available, update the browser you're using regularly or set up automatic updates for the installed apps.
Conclusion - A future without passwords?
There are ongoing discussions about different ways to authenticate.
Electronic ID cards exist, although the current strength of their key pair and encryption might not be the greatest.
You could also move on to use one Single Sign-On service to rule them all. Not only would that give a lot of power to a company that is probably already in a dominant position, but it also requires maximum trust in the implementation. We already do this in some way when we sign in using Google or Facebook etc.
Finally, some new web standard could appear and offer new ways to authenticate.
In any cases passwords are here to stay and will probably always be around so remember how to protect yourself and check that you're safe. Please feel free to share this article would you feel it can be useful to someone else.